
Protecting Smart Homes Against Hackers
20 April 2020 / by Byron BeMiller
Smart homes are booming in popularity. The increasing volume of connected devices that collect data make them an attractive target for hackers. Accordingly, buyers are increasingly concerned about the privacy and security of their smart home data. The combination of LoRa® devices and the LoRaWAN® standard provides powerful levels of security for smart home system consumers.
How Can LoRa Devices Make Homes Smarter?
By implementing a LoRa-enabled smart home solution, customers can manage their home automation across the board. For example, they can use LoRa-enabled sensors to automate the thermostat based on when people are home. Or, they can manage lighting throughout the house, depending on when people enter or exit a room. In particular, sensors with LoRa are well suited for applications which other technologies struggle to cover in terms of range. Outdoor lighting, garage doors, connected pest traps, water leak detection, pool monitoring, outdoor package delivery drop boxes, etc., are all examples of use cases which are ideally suited for sensor devices with LoRa.
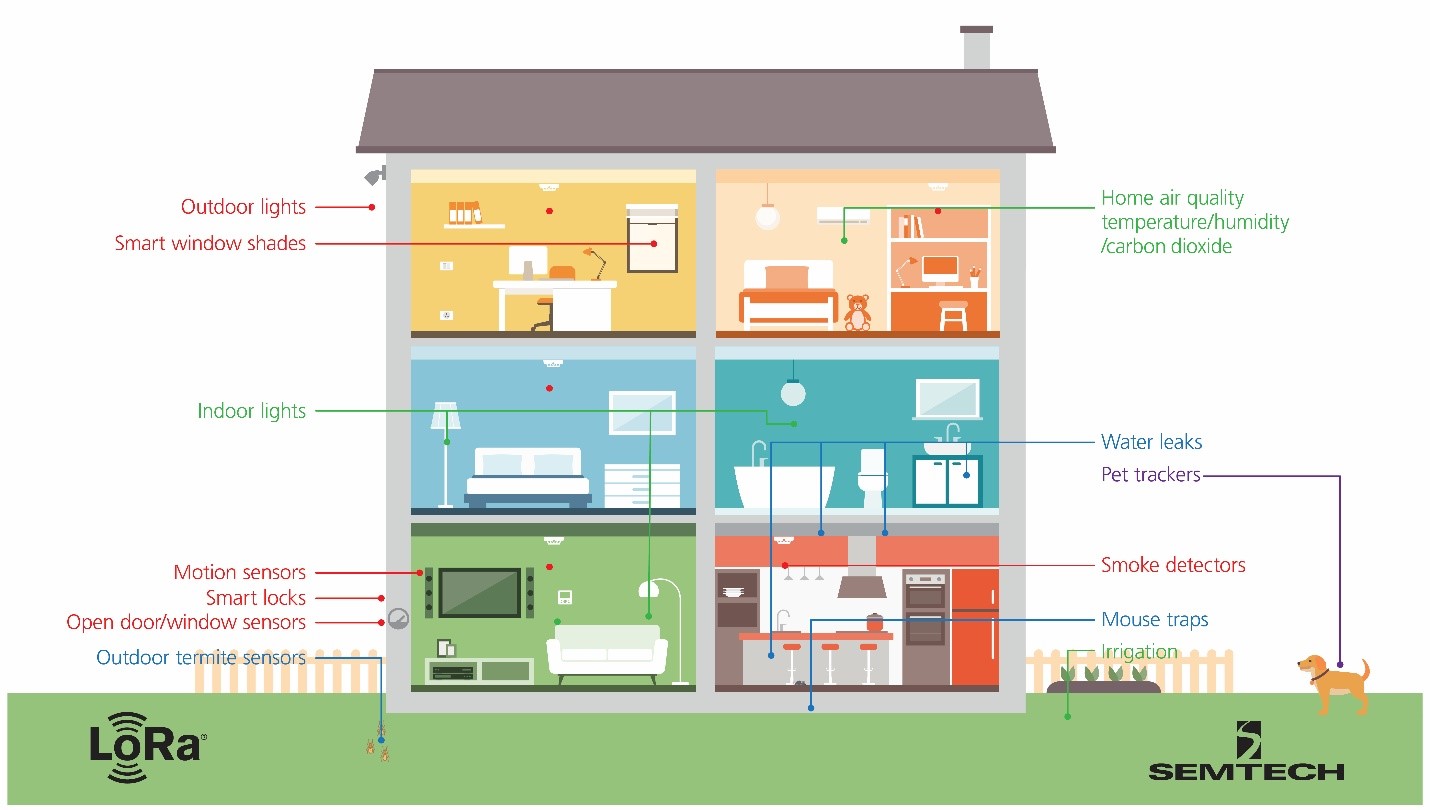
Figure 1: Example of a LoRa-enabled smart home
Smart home systems can be based on LoRa but be implemented with a proprietary protocol developed by the supplier. In those cases, you would need to investigate the underlying security in such a custom protocol. Luckily, there is a standard protocol available on which to rely: LoRaWAN. This article focuses on LoRaWAN security.
What About Traditional Home Security?
When we talk about home security, there are two types of security to consider.
On the one hand, of course, is the traditional type of home security: an automated system that helps prevent burglaries and home invasions by alerting the police when an unauthorized person tries to enter the home. While plentiful options exist in the market, certainly this is something a LoRa-enabled solution can also address. In addition, providers can now up-sell monitoring additional types of connected devices for those use cases which require a larger coverage range to implement.
And yet, that isn’t the only kind of security that is necessary when it comes to smart homes. It is just as important, maybe even more so, to keep your smart home safe from hackers. As smart home security and home automation solutions become more common, so too do attempts to hack both those security and automation systems.
Fortunately, smart home solutions leveraging the LoRaWAN standard are designed with network security in mind.
About LoRaWAN Network Security
The LoRaWAN standard is, by design, very secure. Authentication and encryption are, in fact, mandatory.
A LoRaWAN end device is a sensor or an actuator which is wirelessly connected to a LoRaWAN network through radio gateways using LoRa RF modulation. When manufactured, several unique identifiers are built-in, or “pre-provisioned” on an end device. These identifiers are used to derive security keys that are known only to the device itself, and to the join server, which connects devices to the appropriate LoRaWAN network. Because of the way LoRaWAN networks operate, these secret keys are never exposed. This makes it possible to securely activate and manage the sensors, and makes it very difficult for anyone to hack them.
There are two primary means by which LoRaWAN networks are protected: the join procedure and message authentication. The join procedure establishes mutual authentication between an end device and the LoRaWAN network to which it is connected. Only authorized devices are allowed to join the network.
As illustrated in Figure 2, individual root keys can be securely stored on the end devices, and matching keys are securely stored on the join server.
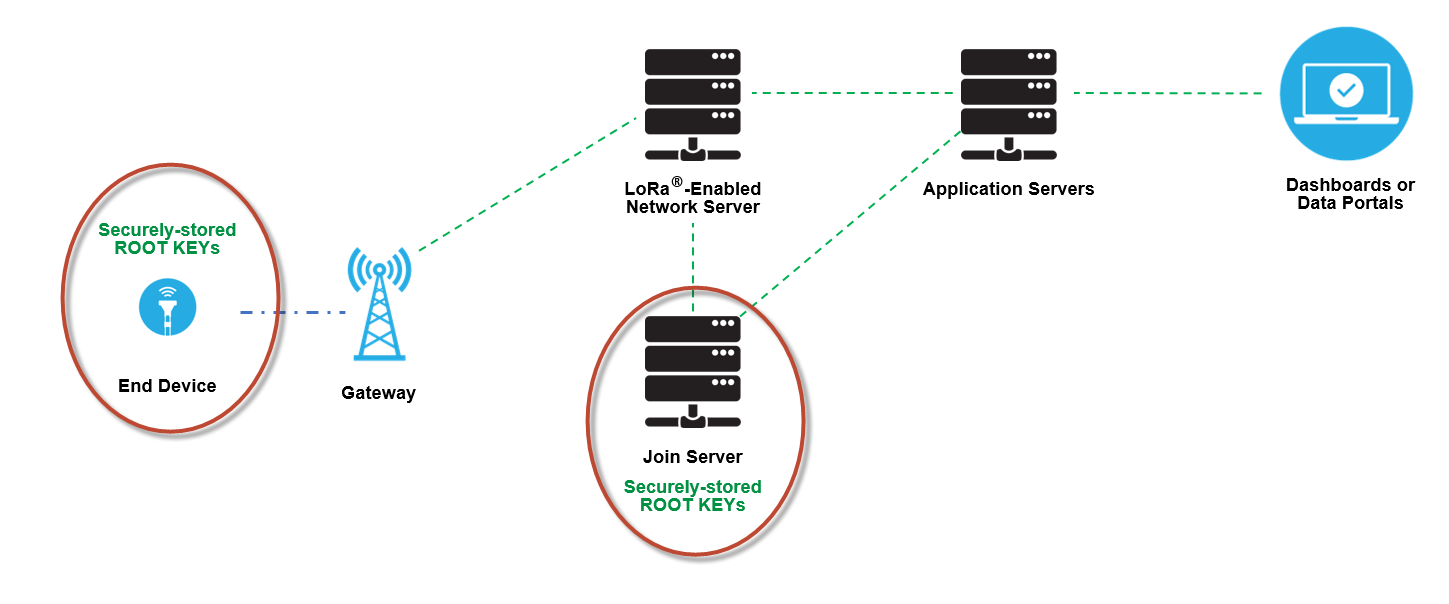
Figure 2: LoRaWAN Network Security Keys
When connecting to a network, the end device sends a request to the join server asking to be added to the network. Once the join server authenticates the device, it returns a join accept message and derives session keys from the pre-provisioned device identifiers and key material. For its part, the end device derives session keys locally as well.
The join server then shares the session keys with the network and application servers, as illustrated in Figure 3.
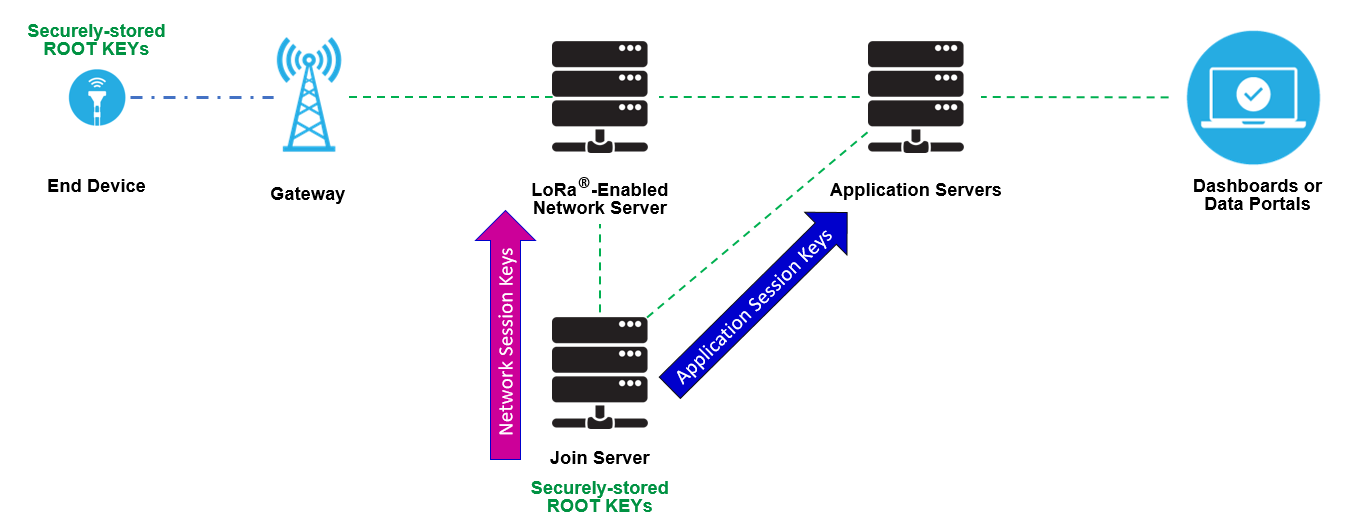
Figure 3: Session Keys Shared with Network and Application Servers
When it comes to the security of the data that is transferred to the network from the end device and vice versa, LoRaWAN MAC and application messages are origin-authenticated, integrity-protected, and encrypted from end-to-end.
These security features ensure that:
-
Network traffic has not been altered
-
Only legitimate devices are connected to the LoRaWAN network
-
Network traffic cannot be listened to (no eavesdropping)
-
Network traffic cannot be captured and replayed
It is important, though, to also note the advice from the LoRa Alliance® Technical Committee regarding full-solution security. It has stated that a fully-secure solution is not only a matter of choosing the right protocol. Like any protocol, it also relies on proper implementation. As shown earlier, LoRaWAN is, by design, very secure. However, networks and devices can be compromised if security keys are not stored safely, not randomized across devices, or if cryptographic numbers that are supposed to be used only once (nonces) are reused.
How then does one avoid using a device that has not implemented these best practices? Luckily, the LoRa Alliance has a LoRaWAN CertifiedCM program which ensures the device has been tested against the standard and works as expected.
Conclusion
The Internet of Things is expanding by leaps and bounds and is being used to provide a great number of conveniences for a great many people, particularly with respect to home automation. This expansion, however, makes connected homes especially attractive to hackers. It is important to verify the security profile of the underlying networking protocol used, and to make sure that a secure protocol is being used and has been implemented properly.
Semtech, the Semtech logo and LoRa® are registered trademarks or service marks of Semtech Corporation or its affiliates.
